Remote Desktop Protocol (RDP) is a powerful Windows feature that allows users to access a computer remotely over the network. While convenient and widely used, it’s also a potential entry point for attackers. Understanding how to check and analyze RDP connection logs can help detect unauthorized access, troubleshoot issues, and maintain system integrity.
In this post, I’ll walk you through everything you need to know about monitoring RDP logs—from accessing the logs to monitoring active remote sessions and centralizing RDP logs with NXLog Platform.
Understanding Remote Desktop logging
Windows logs an event whenever a remote desktop session is initiated, disconnected, or terminated. RDP logs are crucial for security and troubleshooting. They provide the only means to monitor successful versus failed logins, tracking who connected remotely and when, and diagnosing disconnects.
These logs are stored in Windows Event Log and are accessible via the Event Viewer utility. You can find RDP-related events in Event Viewer in the following Windows Logs:
-
Security log — Contains authentication-related events, such as successful or failed login attempts.
-
System log — Includes service-related events, such as RDP service start or stop.
-
Application log — Less frequently used for RDP, but may contain relevant application-level warnings or errors.
On the other hand, you’ll find more specific RDP events under Applications and Services Logs > Microsoft > Windows in the following logs:
-
TerminalServices-RemoteConnectionManager
-
TerminalServices-LocalSessionManager
Setting up Remote Desktop logging
Before you can monitor RDP logs, you must configure logging to capture the relevant events.
To allow RDP logon on a Windows machine:
-
Open Settings > System > Remote Desktop.
-
Toggle the Remote Desktop switch to On.
-
Allow the firewall rule when prompted.
-
Click Remote Desktop users to specify the users or groups who can connect remotely.
Next, configure the relevant RDP logging policies:
-
Open Group Policy Editor (
gpedit.msc). -
Navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy and turn on the following policies:
-
Audit logon events — Success and Failure
-
Audit account logon events — Success and Failure
-
Audit account management — Success and Failure
-
Audit logoff events
-
-
Navigate to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Logon/Logoff and turn on the following policies:
-
Logon — Success and Failure
-
Logoff — Success
-
Special Logon — Success
-
Other Logon/Logoff Events — Success and Failure
-
-
Execute the following command to apply the policy:
> gpupdate /force
Turning on detailed auditing ensures that you record and can trace all remote connections—an essential security best practice.
Key RDP event IDs
Monitoring these RDP activity events will give you detailed insights into who connected, when, and whether they attempted any unauthorized access.
Successful RDP logon
| Event ID | Log | Description |
|---|---|---|
4624 |
Security |
When this event has Logon Type 10 (RemoteInteractive), it indicates a successful RDP logon. |
1149 |
TerminalServices-RemoteConnectionManager |
Logged when a user connects via RDP. |
Failed RDP logon attempt
| Event ID | Log | Description |
|---|---|---|
4625 |
Security |
When this event has Logon Type 10 (RemoteInteractive), it signifies a failed RDP login attempt. Check the failure reason and account name fields. This event is critical for detecting brute-force or unauthorized logon attempts. |
140 |
TerminalServices-RemoteConnectionManager |
Provides more context about failed RDP connection attempts. |
Session connect and reconnect
| Event ID | Log | Description |
|---|---|---|
21 |
TerminalServices-LocalSessionManager |
A user connected to an existng session. |
25 |
TerminalServices-LocalSessionManager |
A user reconnected to an existing session. |
User disconnected
| Event ID | Log | Description |
|---|---|---|
4779 |
Security |
Logged when a user disconnects from an RDP session. |
40 |
TerminalServices-LocalSessionManager |
A user disconnected from an existing session. It could be due to a network interruption or user-initiated. |
24 |
TerminalServices-LocalSessionManager |
A user successfully disconnected from an existing session. |
Differentiating between disconnecting and logging off from an RDP session
So, what is the difference between disconnecting and logging off, and why should you monitor both? Succintly:
-
Disconnecting means the session remains active on the server, but the user has temporarily disconnected from it. All open applications remain running.
-
Logging off ends the session completely. Any open applications are closed, and unsaved work may be lost.
From a security and resource management perspective, users preferably log off. Disconnected sessions still consume memory and could be hijacked if not adequately secured.
How to check Remote Desktop logs
Checking RDP logs is essential for monitoring activity, troubleshooting connection issues, and spotting unauthorized access. Here’s how you can find and interpret Remote Desktop logs.
- Step 1: Open Event Viewer
-
-
Press
Win + R, typeeventvwr.msc, and hitEnter. -
This opens Event Viewer, the tool for viewing all Windows event logs.
-
- Step 2: Navigate to the relevant logs
-
-
Navigate to Windows > Security to view authentication attempts, including successful and failed RDP logins.
-
Navigate to Application and Services Logs > Microsoft > Windows > TerminalServces-LocalSessionManager for RDP session connection and disconnection events.
-
Navigate to Application and Services Logs > Microsoft > Windows > TerminalServces-RemoteConnectionManager to track session state changes like logoff, disconnect, and session creation.
-
- Step 3: Filter by RDP-specific event IDs
-
To narrow down the results:
-
Right-click on a log, for example, Security, then choose Filter Current Log….
-
In the Event IDs field, input key IDs like
4624,4625,4647, and4779.
I explain these event IDs in detail in Key RDP event IDs above.
-
- Step 4: Interpret the event details
-
Once you find a relevant event:
-
Double-click to open it.
-
Review fields like:
-
Account Name – the user attempting the connection.
-
Logon Type – RDP events have Type 10.
-
Source Network Address – the remote IP address.
-
Session ID – used to correlate the session across different events.
-
-
You can also check RDP logs remotely by right-clicking on Event Viewer (Local) and choosing Connect to Another Computer….
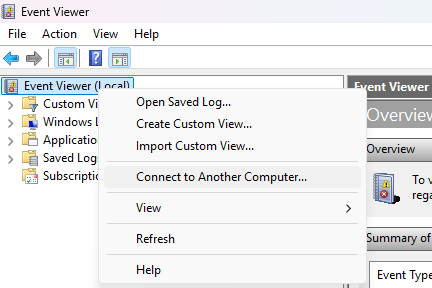
Viewing current Remote Desktop connections
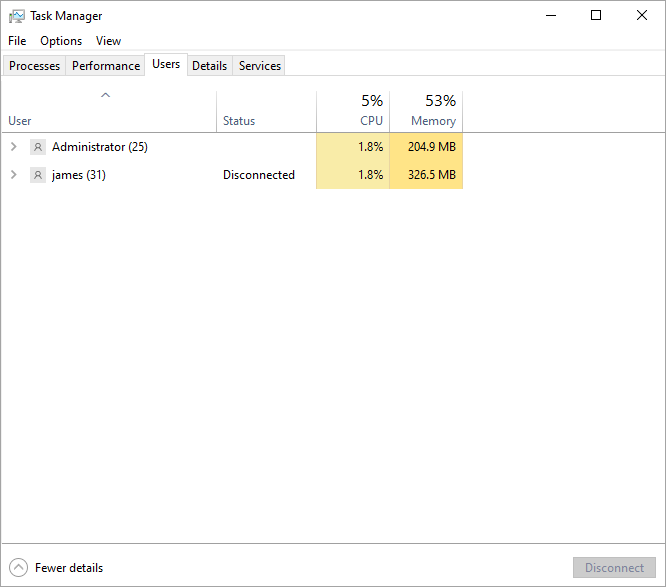
Sometimes, you may need to see who is logged in remotely to a computer. For example, to notify connected users of system changes or to avoid kicking them off during maintenance. Windows provides several session management tools that allow you to view current RDP connections. The most straightforward is from Task Manager.
-
Press
Ctrl + Shift + Escto open Task Manager. -
Switch to the Users tab to display the active sessions, their status, and the user they belong to.
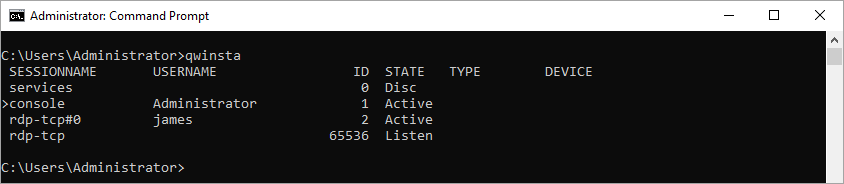
You can also view current RDP sessions from Command Line. The query session and qwinsta commands list all current user sessions, their status, and session IDs.
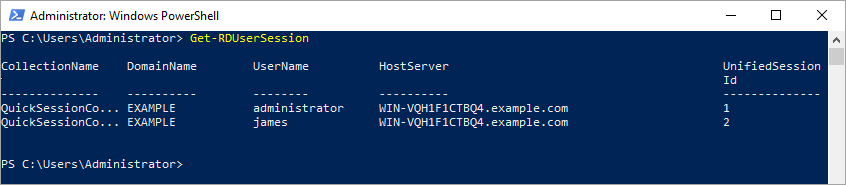
Finally, administrators can query sessions for a Remote Desktop Services deployment using PowerShell. The Get-RDUserSession cmdlet returns a list of all user sessions in a virtual desktop or session collection.
Centralizing and analyzing Remote Desktop logs
Monitoring RDP logs on one or two systems might be manageable manually, but it quickly becomes unscalable in a network with dozens or hundreds of machines. That’s where centralized logging comes into play, and without it, you risk missing critical compromise indicators.
Centralizing RDP logs has several benefits:
-
Consolidation — Aggregate RDP logs from all systems in one place for easier management.
-
Correlation — Identify patterns across multiple systems. For example, simultaneous login attempts.
-
Alerting — Configure real-time alerts on suspicious activities, like multiple failed logins in a short time or logins outside of work hours.
-
Compliance — Maintaining a secure log trail helps meet audit and regulatory requirements.
-
Forensics — In case of a breach, centralized logs help reconstruct attacker activity.
Several tools are available on the market to help you centralize your logs. NXLog Platform provides NXLog Agent, a powerful data collection tool with native support for Windows Event Log, among many other sources. With NXLog Agent, you can easily collect logs from all your RDP-enabled machines and forward them to a central location, including NXLog Platform’s data storage or third-party SIEMs.
Remote Desktop logging and security best practices
Effective logging is only part of securing your Remote Desktop infrastructure. It’s important to follow industry best practices for RDP security and logging to fully leverage logs for defense and detection.
- Restrict RDP access
-
Limit RDP access to specific users and remove unnecessary users from the Remote Desktop Users group. In addition, implement firewall rules or VPN tunneling to limit access to specific IP addresses. You can also use Just-In-Time (JIT) access via tools like Microsoft Defender for Cloud to allow temporary access only when needed.
- Automatically log off idle or disconnected sessions
-
Use Group Policy to configure automatic session timeout for idle users. The
Computer Configuration>Administrative Templates>Windows Components>Remote Desktop Services>Remote Desktop Session Host>Session Time Limitspolicy allows you to set limits for disconnected and idle sessions to free resources and reduce security risk. - Alert on key events
-
It is crucial to set up alerts or dashboards using a SIEM to notify security personnel of anomalies in real time. Such anomalies include:
-
Multiple failed login attempts (Event ID 4625).
-
Unexpected logons (Event ID 4624 from unknown IPs or accounts).
-
Sessions during odd times or from unusual geographic locations.
- Aggregate logs in a central location
-
Use centralized logging tools like NXLog Agent, Sysmon, or Windows Event Forwarding (WEF) to collect logs from all RDP-enabled machines and store them in a central location. Centralizing logs makes it easier to detect coordinated attacks or policy violations.
- Enable and protect audit logs
-
Ensure you retain logs for a sufficient period and use log integrity measures. For example, read-only access or write-once logging systems. In addition, log files should be regularly backed up and protected from tampering.
- Regularly review and fine-tune logging policies
-
Review the events you’re logging to ensure you’re capturing what you need without overloading storage. Update filters and queries as needed to align with evolving threats and business requirements.
By following these best practices, you’ll improve your ability to detect and respond to security incidents, optimize system performance, and comply with industry standards.
How NXLog Agent helps forward, analyze, and centralize Remote Desktop logs
NXLog Agent is widely used for aggregating, parsing, and forwarding logs to SIEMs and log analytics platforms. Key features for RDP monitoring include:
-
Windows Event Log support — NXLog Agent can collect logs locally or remotely from all the channels relevant to RDP, including custom channels like
Microsoft-Windows-TerminalServices-*. -
Log parsing and filtering — You can configure NXLog Agent to extract and forward only relevant RDP events using filters based on event IDs.
-
Log forwarding — Forward logs to centralized log storage in standard formats like JSON, XML, or syslog.
-
Secure transport — Supports encrypted log forwarding using TLS/SSL to protect log integrity.
-
Lightweight agent — It runs efficiently on both Windows clients and servers with minimal overhead.
Conclusion
RDP is a vital tool for modern IT operations, but it also introduces security and visibility challenges that you cannot ignore. Monitoring Remote Desktop logs is not just about keeping an eye on who’s connecting; it’s about maintaining control, detecting threats, and ensuring accountability.
- Key takeaways
-
-
RDP activity is fully traceable through Windows Event Log, especially the Security and TerminalServices logs.
-
Event Viewer is a powerful tool for checking RDP logs and filtering for key event IDs like
4624,4625,4647, and4779. -
Real-time monitoring of successful logins, failed attempts, and disconnections is critical for detecting intrusions or policy violations.
-
Centralized logging tools like NXLog Agent greatly enhance manageability and visibility across multiple systems.
-
Security hygiene matters — enforcing strong authentication, restricting access, and logging out idle sessions are just as important as logging.
-
- Final recommendations
-
-
Enable detailed auditing policies on all RDP-enabled machines.
-
Use centralized logging to correlate data and respond faster to threats.
-
Review logs regularly — automation is ideal to catch red flags early on.
-
Harden your RDP settings using best practices, including Network Level Authentication and IP restrictions.
-
By combining strong controls with effective monitoring, you can turn Remote Desktop from a potential risk into a secure, reliable management tool. Implement these practices today to gain full visibility into RDP activity and improve your organization’s overall security posture. Don’t leave your RDP sessions unwatched. Monitor, alert, and protect.
