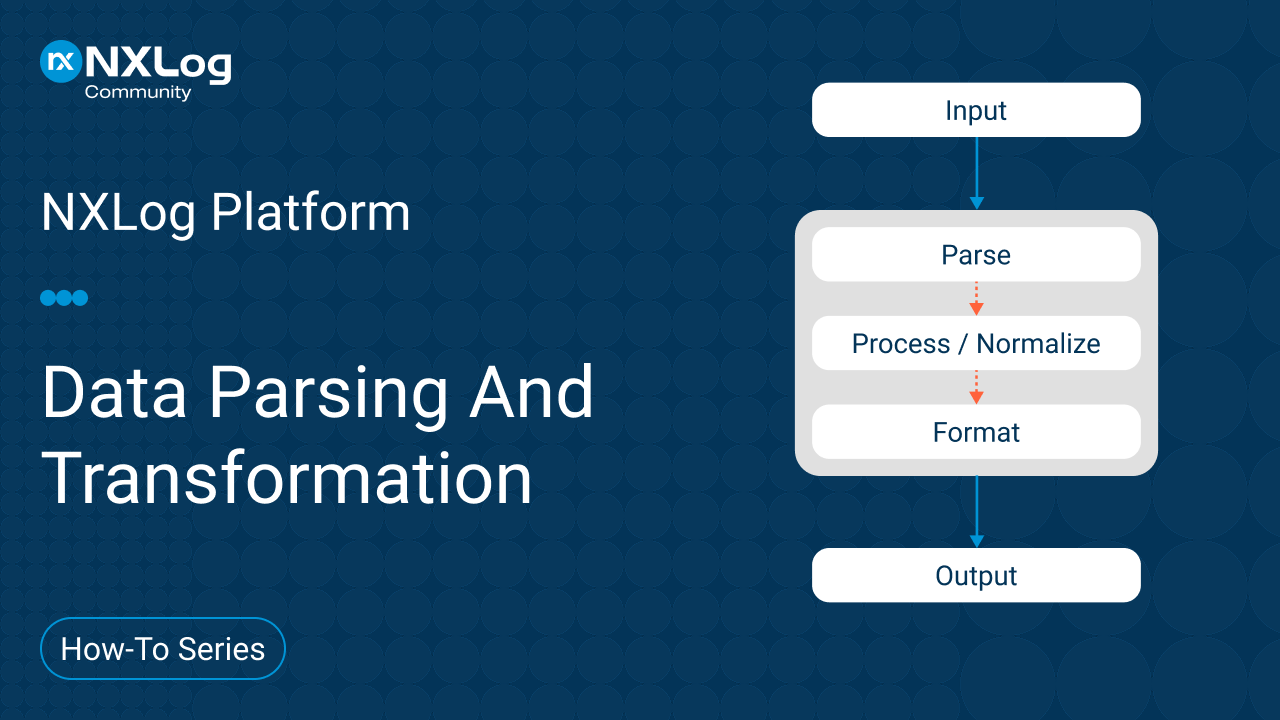
Ensuring that users only see the log data relevant to their role is essential for both security and compliance. In this video tutorial, we walk through configuring access rules in NXLog Platform to control permissions for specific log types, showing how to define rules for different users and validate them by testing access under separate accounts.