Data logging and event monitoring have become essential to provide security and performance monitoring of business operations. However, the vast volume of logs generated can lead to significant challenges, including high costs and inefficiencies.
Many companies collect an excessive number of logs, often missing out on the most critical security-related events. The majority of these logs, known as log noise, offer little to no value to security analysts and can obstruct timely access to high-priority security events. This low ratio between high-value events and log noise can severely impact the effectiveness of security monitoring.
Moreover, the sheer volume of collected logs introduces substantial challenges in terms of data storage, retention, and maintenance. The complexity and expense of managing an end-to-end logging infrastructure can quickly escalate, making it crucial for businesses to find efficient solutions. You will quickly reach this predicament in high-volume logging environments, requiring a resilient log management system.
This article will help you develop a log management strategy that ensures reliable log analytics and optimized performance while reducing the overall logging stack costs. To do so, we’ll consider the challenges to address, discuss best practices and detail how NXLog Platform is uniquely positioned as an all-in-one log management platform to help reduce log storage costs and also reduce log management costs.
Log management cost challenges
These are main challenges to consider for both an affordable and cost-effective log management and cost-efficient log search:
-
How data volume growth impacts your storage costs
Logs can grow exponentially, especially in larger system architectures. Storing all logs indefinitely drives up storage and processing costs.
-
Balancing data retention and observability needs
It’s often a delicate balance deciding which data to retain, aggregate, or discard. Over-retention leads to bloated indices and higher costs, while aggressive filtering risks losing critical diagnostic data.
-
Overhead effort required for integration and toolchain development
Seamlessly connecting all elements of your log management system is an ever-evolving task, as each source and destination may require maintenance or integration with other elements. Integrating, maintaining, and scaling your log management system can require expertise and constant tuning to maintain cost efficiency.
From these challenges we can define key techniques to cut logging costs:
-
Efficiently store log data.
-
Reduce log data volume and content.
-
Simplify your log collection architecture.
All of these decisions influence, directly and indirectly, your log management cost optimization. The complexity and expense of managing an end-to-end logging infrastructure can quickly escalate, making it crucial for businesses to find efficient solutions.
Why logging volume inflates costs
How do you go about weeding out low-value events while ensuring that you keep the high-value ones? Are there any additional pros or cons to such an approach?
To achieve the goal of collecting mainly high-value events, you need to collaborate with the key stakeholders in your organization who will be using the logs. Establish a list of event types that are most critical to the security and performance of your business operations, keeping in mind that your organization may be legally responsible for collecting additional types of events to fulfill compliance mandates and auditing requirements.
After identifying these critical event types, work with your IT security team to document the attributes of these events so they can be programmatically identified and collected for future processing and analysis. For more details on this approach, see our white paper, How to develop a log collection strategy for cost-efficient logging.
How NXLog Platform can help
Regardless of your organization’s size, industry, or current logging infrastructure, NXLog Platform’s flexibility as a on-prem log management solution provides numerous ways to reduce log noise and volume, which can significantly reduce operational costs.
There is practically no other affordable log management solution capable of collecting logs from all operating systems and devices found in larger organizations, including multiple UNIX variants, Linux, Windows, macOS, along with various network-ready devices. NXLog Platform excels at filtering, aggregating, and either storing logs directly or sending them to almost any SIEM or endpoint of your choice.
NXLog Platform is a one-stop solution for managed log collection, processing, storage, visualization, and distribution. It doesn’t require you to install third-party plugins or different connectors each time you decide to use a different log source or third-party target system. Instead, NXLog Platform includes a growing collection of configuration templates that greatly simplifies and accelerates the integration of the most common log sources with your preferred SIEM.
Reducing SIEM and storage costs
The flexibility and comprehensive features of NXLog Platform help reduce both SIEM licensing costs (typically related to the volume of ingested logs) and SIEM logging costs.
- Trimming events and filtering logs
-
NXLog Platform reduces event noise by trimming events and filtering logs. Trimming events refers to reducing log size by removing unwanted data, such as fields containing low-value information, and redundant or duplicated fields. Filtering allows excluding entire log events when they provide no valuable information or are duplicates. NXLog Platform can filter events based on nearly any set of criteria, resulting in a log volume reduction.
These techniques help reduce SIEM costs by attacking log data bloat, assuring log data reduction without losing crucial information and that only high-value events needed by security analysts are sent to your SIEM. This creates a SIEM cost reduction in log ingestion and analysis.
- Data compression
-
Log data can be compressed during transmission or when writing logs to files. This reduces network bandwidth usage and reduces storage costs if the endpoints are writing log data to files.
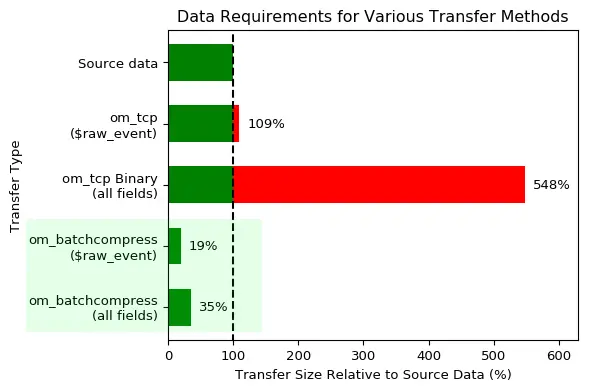
- Efficient storage solutions
-
By leveraging NXLog Platform’s out-of-the-box log storage for non-security or lower-priority events, you can send less data to your SIEM, significantly reducing costs.
Simplifying the logging stack
NXLog Platform lowers the complexity of your logging stack, leading to considerable budget and resource savings.
- Simple agent fleet management
-
With NXLog Platform, you only need one agent software to handle all log collection, filtering, and processing tasks. This reduces the budget and human resources required for integration and maintenance. Efficient agent fleet management capabilities further reduce costs associated with configuring and monitoring a large number of agents across your network and infrastructure.
- Comprehensive integrations
-
NXLog Platform offers over 100 popular integrations with log sources and target systems out-of-the-box. This ensures a fast and streamlined deployment of the solution, thus helping save on integration efforts.
- Full observability solution
-
NXLog Platform includes out-of-the-box storage and analytics solutions. This eliminates the need for extra third-party products along with the added burden of integrations and ongoing maintenance.
Conclusion
Reviewing the log management cost challenges detailed earlier and how NXLog Platform handles them:
| Challenge | NXLog Platform answer |
|---|---|
How data volume growth impacts your storage costs |
Highly efficient data compression and data selection options such as trimming and filtering. |
Balancing data retention and observability needs |
Built-in analytics, retention and log search features. |
Overhead effort required for integration and toolchain development |
Complements its all-in-one full observability solution with wide integration support for third-party components. |
We explored how NXLog Platform helps businesses significantly cut down on the costs associated with log management while enhancing their security posture through efficient and effective log handling. The cost savings resulting from these log management best practices can be especially significant if your organization is currently sending all events unfiltered to a SIEM, as many of them charge by data volume ingested.
NXLog Platform’s rich set of features, including a modular and distributed architecture and seamless integration with a vast number of third-party solutions, make it a highly cost-effective choice for optimizing your logging infrastructure and ensuring robust security operations.
