On February 26, 2024, the U.S. National Institute of Standards and Technology (NIST) officially released Cybersecurity Framework (CSF) 2.0. This release has had the most significant changes since its inception in 2014. Let’s quickly walk through the updates it brought and how log collection supports the functions of the renewed framework.
What is NIST CSF
The U.S. NIST Cybersecurity Framework is one of the most widely used security frameworks (with ISO27001, CIS, and others), helping organizations estimate, manage, and reduce their cybersecurity risks. It was initially published in 2014 as a response to "Executive Order 13636: Improving Critical Infrastructure Cybersecurity" issued by President Obama in Feb 2013. The order requested the design of a voluntary cybersecurity framework. This framework consists of standards, guidelines, and best practices. Its purpose is to help the nation’s critical infrastructure organizations, including financial, energy, health care, and others. The goal is to better protect their information and physical assets from cyberattacks. The framework was created through public-private collaboration. It serves a crucial role by providing a common language to address and manage cyber risk. This is achieved cost-effectively based on business needs. Moreover, it accomplishes this without imposing additional regulatory requirements on businesses.
NIST CSF went through the years with just one minor 1.1 update in 2018. Ten years later, the threat landscape has changed significantly, and NIST proposed version 2.0, which is quite a change to adapt the framework to the latest cybersecurity best practices. While the core structure of the NIST CSF stays the same in general, proposed changes enhance the framework’s capabilities.
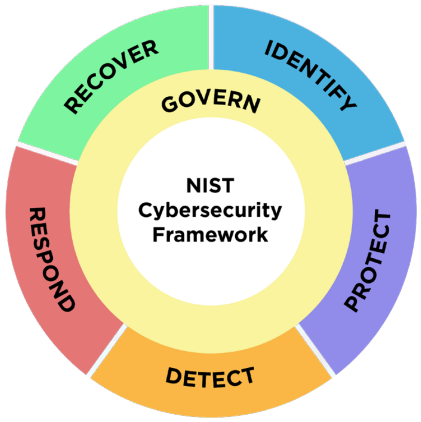
The framework is structured around a set of high-level core functions, which are essential for any cybersecurity program. They include Identify, Protect, Detect, Respond, Recover, and, with the latest update, Govern. This structure provides a strategic overview of an organization’s approach to cybersecurity risk management. Those six core functions are broken down into 22 categories and 106 subcategories. Each subcategory is an atomic control, which defines best practices to consider when assessing an organization’s cybersecurity program. It is essential to highlight that NIST CSF is vendor-agnostic and non-prescriptive. Consider the framework as a tool rather than a checklist to follow.
What’s changed in CSF 2.0?
As you know, the initial version of CSF focused on the nation’s critical infrastructure. The introduction of CSF 2.0 officially broadened its reach, since it now includes all sorts of organizations, not just those deemed necessary. The next major shift was adding a new top-level "Govern" function, which includes many function categories to align with modern security risk management best practices.
Another structural change in CSF 2.0 is noteworthy, in that it introduces 'implementation examples'. These examples help organizations translate the framework’s technical requirements into actual improvements in security posture and ensure alignment with business objectives. Also, CSF 2.0 established a direct connection with other security frameworks to build a holistic vision for cybersecurity.
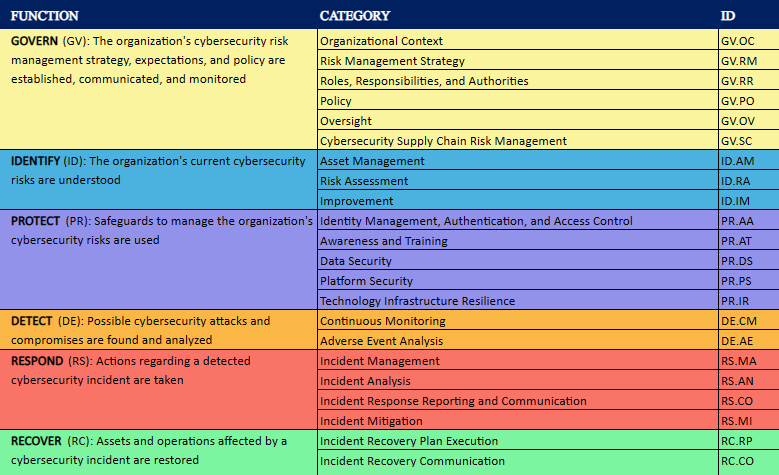
Previously, "cybersecurity supply chain risk management" was mixed into different functions. Now, it has become a separate sub-category under the Govern function. This change highlights the importance of supply chain management. It follows the transformation trend of the Risk Management Framework (NIST 800-37) and the Controls Catalog (NIST 800-53), with both moved software supply chain security to dedicated sections in the latest revisions.
How NXLog helps comply with NIST CSF 2.0
NXLog Enterprise Edition enables an autonomous pipeline to support security monitoring systems (SIEM, UEBA, XDR, APM, and others) with the necessary log data for ongoing analysis.
NXLog helps to implement the PROTECT function in the “Platform Security“ category.
| CSF Subcategory | Implementation Examples | Informative Reference | NXLog |
|---|---|---|---|
PR.PS-04: |
Example 1: |
NIST Special Publication 800-218, Secure Software Development Framework (SSDF) Version 1.1: Recommendations for Mitigating the Risk of Software Vulnerabilities: PO.3.3 |
NXLog Enterprise Edition lets you capture logs generated by operating systems (Windows, Linux, macOS, AIX, Solaris, BSD, etc.) and applications. It provides over a hundred integrations out-of-the-box to ensure you can deliver all your valuable log data to the right place (SIEM or APM) for ongoing monitoring. |
NXLog supports “Data Security” (PR.DS) category implementation about logs data, whether the data is at rest or in transit.
| CSF Subcategory | Implementation Examples | Informative Reference | NXLog |
|---|---|---|---|
PR.DS-01: |
Example : |
NIST Special Publication 800-218, Secure Software Development Framework (SSDF) Version 1.1: Recommendations for Mitigating the Risk of Software Vulnerabilities: PS.1.1 |
The File Integrity Monitoring (FIM) feature of NXLog Enterprise Edition can scan files and directories and report detected changes. |
PR.DS-02: |
Example: |
CIS Controls: 3.10 |
NXLog Enterprise Edition has an SSL/TLS module to provide secure transport for log messages. NXLog Enterprise Edition supports certificates with TPM-generated keys. Trusted Platform Module (TPM) chips provide tamper-resistant security functions, making it the most secure way of encrypting data. |
PR.DS-11: |
Example: |
NIST Special Publication 800-218, Secure Software Development Framework (SSDF) Version 1.1: Recommendations for Mitigating the Risk of Software Vulnerabilities: PS.3.1 |
NXLog Enterprise Edition can route log streams to multiple destinations and automate log rotation. Together with the NXLog FIM module, it allows you to build a robust backup pipeline. |
NXLog Enterprise Edition also complements the “Technology Infrastructure Resilience” (PR.IR-03 and PR.IR-04) category within the PROTECT function by providing robust log collection architecture capabilities.
| CSF Subcategory | Implementation Examples | Informative Reference | NXLog |
|---|---|---|---|
PR.IR-03: |
Example 1: |
CRI Profile Version 2.0: PR.IR-03 |
NXLog Enterprise Edition allows for high-availability deployments. NXLog integrates with third-party load-balancing solutions and ships with built-in failover capabilities. See the High Availability section in the NXLog agent User Guide for more information. |
Finally, as a powerful and versatile log collection and shipping software, NXLog Enterprise Edition helps implement the core DETECT function of the framework, including "Continuous Monitoring" (DE.CM) and "Adverse Event Analysis" (DE.AE) category controls.
| CSF Subcategory | Implementation Examples | Informative Reference | NXLog |
|---|---|---|---|
DE.CM-01: |
Example 1: |
CIS Controls: 13.1 |
NXLog Enterprise Edition can monitor and proactively analyze Domain Name Server (DNS) queries and responses. See the DNS Monitoring section in the NXLog agent User Guide for more information. NXLog also allows for passive network monitoring by generating logs for various protocols. It uses the |
DE.CM-02: |
Example: |
CRI Profile Version 2.0: DE.CM-02 |
NXLog Enterprise Edition allows the capture of logs from physical access control systems and sending them for centralization and analysis. |
DE.CM-03: |
Example 1: |
CIS Controls: 10.7 |
NXLog helps integrate all valuable logs into monitoring systems and ensures nothing is missed. NXLog Enterprise Edition is compatible with all the major SIEM/UEBA/XDR systems, such as Google Chronicle, Microsoft (Azure) Sentinel, MicroFocus ArcSight, IBM QRadar, and others. |
DE.CM-09: |
Example 1: |
CIS Controls: 10.1 |
NXLog Enterprise Edition allows you to capture and centralize logs from operating systems and applications, including those stored in files and database structures, sent over network sockets, and others. NXLog helps collect all valuable logs and analyze them properly in the security system. |
DE.AE-02: |
Example 1: |
CIS Controls: 8.11 |
NXLog Enterprise Edition allows you to analyze your log data on the fly, trigger events in real-time, filter data, and send it for correlation analysis to SIEM systems. NXLog provides powerful data filtration and transformation capabilities to offload your SIEM system, make security analysis more efficient, and save storage costs. |
DE.AE-03: |
Example 1: |
CRI Profile Version 2.0: DE.AE-03 |
NXLog allows you to capture security and audit logs from various data sources, including operating systems, applications, and network devices, and send them to SIEM for correlation. You can also simultaneously route the collected data to other destinations, such as a log backup storage. |
