File access auditing is the process of tracking who reads, modifies, or deletes files on a system, providing a record of user activity for security and compliance purposes. On Windows systems, this is especially important for monitoring sensitive or business-critical files, such as financial records, HR data, or confidential customer information, where unauthorized access could result in a data breach or regulatory violation.
In this post, I’ll show you how to enable file access auditing on Windows and use NXLog Agent to collect and forward file access events to help you protect sensitive data and meet compliance requirements.
Why monitor file access on Windows?
Files are one of the primary ways to store and share information, often containing valuable and sensitive data. From business plans and financial records to confidential customer information, these are exactly the kinds of files attackers target. Monitoring who accesses or attempts to access these files helps you detect suspicious activity and protect your organization’s most critical assets.
- Monitor assignment of secure access controls
-
Almost all compliance mandates start by implementing protection for files containing sensitive data. Questions you may ask:
-
Are the correct permissions assigned based on users' job roles?
-
Are permissions set for the correct users or groups?
-
Are the users making changes that they are allowed to make?
-
- Monitor access to protected data
-
Compliance is a continuous journey in which you must ensure your environment complies with regulations. Your security team must have visibility of who is accessing files, when, and from where. Having this information in real-time is paramount to remaining vigilant against inappropriate access by malicious insiders and external attackers.
- Measure access control strength
-
Unfortunately, it’s common for IT teams to let Active Directory evolve organically. Group memberships are rarely audited, let alone permissions and nested group memberships, resulting in users having permission to access data they should not have.
- Detect breaches
-
While organizations want to avoid a data breach and, therefore, a compliance violation, the possibility remains. Thankfully, as long as you’re monitoring your Windows file server, there will be definite indicators. If you have file access auditing configured correctly, you should be able to detect abnormalities, such as file access during irregular times or large amounts of data copied in a short period.
Configuring file access auditing on Windows
There are two simple things you need to do in Windows to enable file access auditing:
-
Configure the Audit Object Access policy via Group Policy.
-
Configure file auditing on the file or folder you want to monitor.
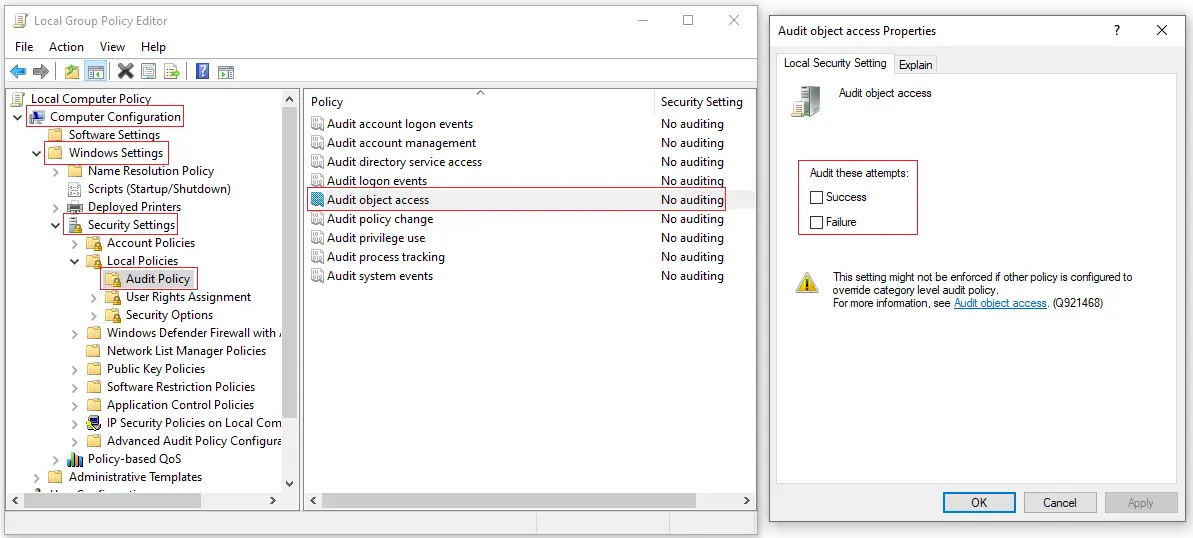
Configuring Audit Object Access via Group Policy
You can configure file access auditing by opening Group Policy Editor and activating the policy under Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy.
The image below shows the Local Group Policy Editor in Windows 10. However, these auditing steps apply to any modern Windows OS, whether you’re monitoring a Windows workstation or a Windows Server file share.
Configuring file auditing for a file or folder
Microsoft has a great guide on configuring file auditing: Apply a basic audit policy on a file or folder.
Once you configure file auditing, Windows logs two events to the Security log recording file access:
-
Event ID 4663 - An attempt was made to access an object.
-
Event IT 4656 - A handle to an object was requested.
You can check the file access history in Event Viewer by looking under Windows Logs > Security. Filter the log for event IDs 4663 and 4656 to find entries of file access attempts. However, the real value comes when you start collecting and monitoring these events in your SIEM or observability platform.
Auditing Windows file access with NXLog Agent
Once you configure file access auditing and the events in question are in Windows Event Log, you will need to collect and forward them to the destination. NXLog Agent is the perfect tool for this job and can help simplify your file access monitoring toolchain.
This configuration uses the Event Log for Windows input module to collect event IDs 4656 and 4663.
It then converts the events to JSON format and writes them to a file.
<Extension json> (1)
Module xm_json
</Extension>
<Input file_access>
Module im_msvistalog
<QueryXML>
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[(EventID=4656 or EventID=4663)]]</Select>
</Query>
</QueryList>
</QueryXML>
</Input>
<Output file>
Module om_file
File 'C:\logs\windows_events.log' (2)
Exec to_json(); (3)
</Output>
<Route r1>
Path file_access => file
</Route>| 1 | The JSON extension is required to convert the events to JSON format. |
| 2 | Change the output file path for your environment. |
| 3 | Calls the JSON extension’s to_json() procedure to convert the event to JSON. |
The following is a sample event ID 4663 after it was processed by the NXLog Agent configuration above. It is pretty-printed for readability.
{
"EventTime": "2023-05-02T00:51:53.200993-07:00",
"Hostname": "FILESRV-01",
"Keywords": "9232379236109516800",
"LevelValue": 0,
"EventType": "AUDIT_SUCCESS",
"SeverityValue": 2,
"Severity": "INFO",
"EventID": 4663,
"SourceName": "Microsoft-Windows-Security-Auditing",
"ProviderGuid": "{54849625-5478-4994-A5BA-3E3B0328C30D}",
"Version": 1,
"TaskValue": 12800,
"OpcodeValue": 0,
"RecordNumber": 866208,
"ExecutionProcessID": 4,
"ExecutionThreadID": 7792,
"Channel": "Security",
"Message": "An attempt was made to access an object.\r\n\r\nSubject:\r\n\tSecurity ID:\t\tS-1-12-1-3226568308-1140053887-2796057524-3382768311\r\n\tAccount Name:\t\tJohnDoe\r\n\tAccount Domain:\t\tMYDOMAIN\r\n\tLogon ID:\t\t0x3D62A\r\n\r\nObject:\r\n\tObject Server:\t\tSecurity\r\n\tObject Type:\t\tFile\r\n\tObject Name:\t\tC:\\test\r\n\tHandle ID:\t\t0x2960\r\n\tResource Attributes:\tS:AI\r\n\r\nProcess Information:\r\n\tProcess ID:\t\t0x11a0\r\n\tProcess Name:\t\tC:\\Windows\\explorer.exe\r\n\r\nAccess Request Information:\r\n\tAccesses:\t\tReadData (or ListDirectory)\r\n\t\t\t\t\r\n\tAccess Mask:\t\t0x1",
"Category": "File System",
"Opcode": "Info",
"Level": "Information",
"SubjectUserSid": "S-1-12-1-3226568308-1140053887-2796057524-3382768311",
"SubjectUserName": "JohnDoe",
"SubjectDomainName": "MYDOMAIN",
"SubjectLogonId": "0x3d62a",
"ObjectServer": "Security",
"ObjectType": "File",
"ObjectName": "C:\\test",
"HandleId": "0x2960",
"AccessList": "%%4416\n\t\t\t\t",
"AccessMask": "0x1",
"ProcessId": "0x11a0",
"ProcessName": "C:\\Windows\\explorer.exe",
"ResourceAttributes": "S:AI",
"EventReceivedTime": "2023-05-02T00:51:54.825393-07:00",
"SourceModuleName": "file_access",
"SourceModuleType": "im_msvistalog"
}Windows file auditing events provide an overwhelming amount of detail, some of which might not be useful to you. NXLog Agent can also help you reduce log noise and streamline data for analysis by trimming and renaming fields.
This configuration uses the Event Log for Windows input module to collect event IDs 4656 and 4663.
It also uses the Rewrite extension to retain only a subset of file access event fields.
Finally, it converts the events to JSON format and writes them to a file.
<Extension json>
Module xm_json
</Extension>
<Extension rewrite>
Module xm_rewrite
Keep EventTime ,Hostname, EventType, EventID, Category, SubjectUserName, SubjectDomainName, ObjectType, ObjectName,
Rename SubjectUserName, Username
Rename SubjectDomainName, Domain
</Extension>
<Input file_access>
Module im_msvistalog
<QueryXML>
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">*[System[(EventID=4656 or EventID=4663)]]</Select>
</Query>
</QueryList>
</QueryXML>
Exec rewrite->process(); (1)
</Input>
<Output file>
Module om_file
File 'C:\logs\windows_events.log' (2)
Exec to_json(); (3)
</Output>
<Route r1>
Path file_access => file
</Route>| 1 | Calls the Rewrite extension’s process() procedure to trim and rename fields. |
| 2 | Change the output file path for your environment. |
| 3 | Calls the JSON extension’s to_json() procedure to convert the event to JSON. |
The following is a sample event ID 4663 after it was processed by the NXLog Agent configuration above. As you can see, it is much more readable than the original event. Additionally, the difference between the two output files is 1.9 KB versus 278 bytes, the latter being seven times smaller.
{
"EventTime": "2023-04-27T22:52:26.138469-07:00",
"Hostname": "FILESRV-01",
"EventType": "AUDIT_SUCCESS",
"EventID": 4663,
"Category": "File System",
"Username": "JohnDoe",
"Domain": "MYDOMAIN",
"ObjectType": "File",
"ObjectName": "C:\\test"
}Conclusion
Monitoring file access on Windows is critical in protecting sensitive data and ensuring compliance with security standards. By enabling auditing and using NXLog Agent to collect and process file access events, you can gain full visibility into who is accessing what, when, and how. This not only strengthens data protection but also streamlines compliance reporting and incident response.
If you’re looking for a reliable and flexible file access monitoring tool, talk to us. Our team can help you design and deploy a logging pipeline that fits your organization’s needs.
