DNS logging with NXLog
Attackers are using DNS for data theft, denial-of-service, and other malicious activity. Proactive monitoring of DNS activity can help network administrators quickly detect and respond to these threats.
Enterprise-grade DNS log collection and enrichment
There are few things more important to the operation of the Internet than DNS. We rely on DNS for translating easy-to-remember website names into the cryptic , numeric IP addresses needed to make such navigation possible. Although DNS is a very mature technology — it has been an invaluable Internet service since 1985 — it still has some vulnerabilities. DNS was designed during an era when cyberattacks were unheard of, and consequently, network security was of little or no concern.
In today’s world, network-ready, DNS-dependent devices are ubiquitous as well as the attacks that are mounted on them. Attackers frequently use DNS for data theft , denial-of-service, and other malicious activity. Without DNS logging, some types of security breaches would go completely undetected until the consequences of such a breach reveal some irreparable damage, only to be noticed days or weeks later.
Security advantages of DNS logging
- By proactively monitoring DNS audit logs, network administrators can quickly detect and respond to cyberattacks.
- Forwarding DNS logs to a SIEM allows breaches to be quickly detected thus reducing the response time needed for mending security holes and deploying countermeasures.
- With an effective logging strategy responsible for forwarding quality events to a SIEM, the brunt of intrusion detection can be automated, giving security operations center (SOC) personnel more time for analyzing suspicious alerts and working on security tasks of a more proactive nature.
- Aggregating DNS logs using a centralized log collection strategy while filtering out low-quality events can significantly boost threat detection efficiency. Some fringe benefits of this approach are:
- The cost of storage and processing are reduced since filtering drops the majority of events which are of little or no security interest.
- Event correlation is much easier to realize with streams of events being sent to a centralized logging server where they are aggregated.
- GDPR and other compliance obligations are more easily fulfilled when combined with this centralized architecture and the ability to filter and securely forward specific events needed for compliance to a secure storage location for archival.
Download White Paper
The Importance of DNS Logging in Enterprise Security
How NXLog Platform can help with DNS monitoring
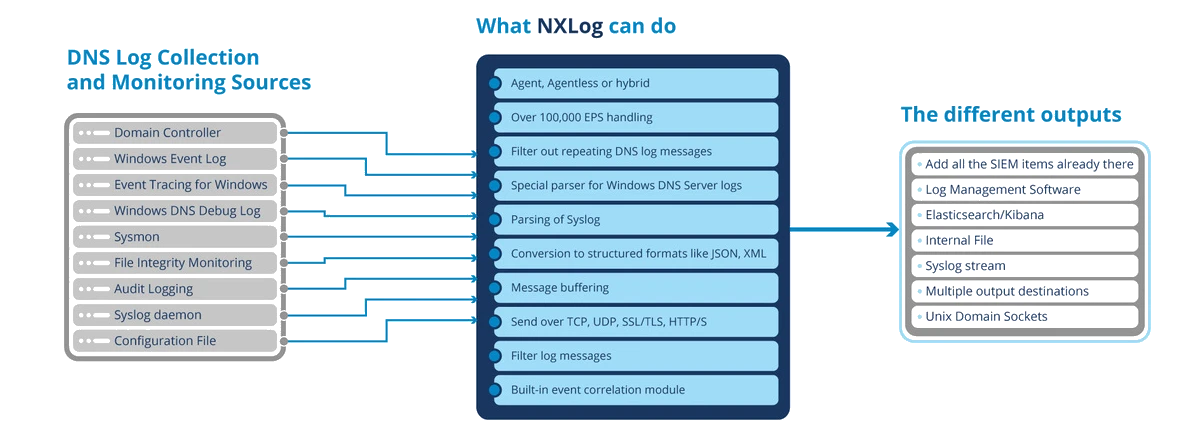
NXLog Platform provides several unique features for collecting and processing DNS logs.
Log collection infrastructure with NXLog
NXLog offers seamless integration between a wide variety of log sources and various output streams commonly used by popular solutions for ingesting and analyzing security events.